An Ontology for Trust Recommendation in Social Internet of Things
Latest version: https://liidr.org/trust-recommendation-in-social-internet-of-things/
Permanaent IRI for this version (v1.0.0): https://liidr.org/trust-recommendation-in-siot-specification/1.0.0/index.html
Creators
- Marius Becehrer | m.becherer@adfa.edu.au
- Omar K. Hussain | o.hussain@adfa.edu.au
- Frank den Hartog | frank.den.hartog@unsw.edu.au
- Yu Zhang | michael.y.zhang@adfa.edu.au
- Elizabeth Chang | e.chang@griffith.edu.au
Abstract
This ontology models trust recommendation concepts in SIoT to bridge the gap between abstract trust concepts and real-world device concepts.
Table of Content
- Table of Content
- Key Compositions of TRESIOT ontologies
- Trust Recommendation
- Transaction Context
- Relationship
- Network
- Node
- Trustor and Trustee
- Specification
Key Compositions of TRESIOT ontologies
The TRESIOT ontology presents the entities of trust recommendation and their relationships in the domain of the Social Internet of Things. In this context, the basic elements of the ontology include Node, Trustor, Trustee, Trust Recommendation, Transaction Context, Relationship and Network as illustrated in the figure below.
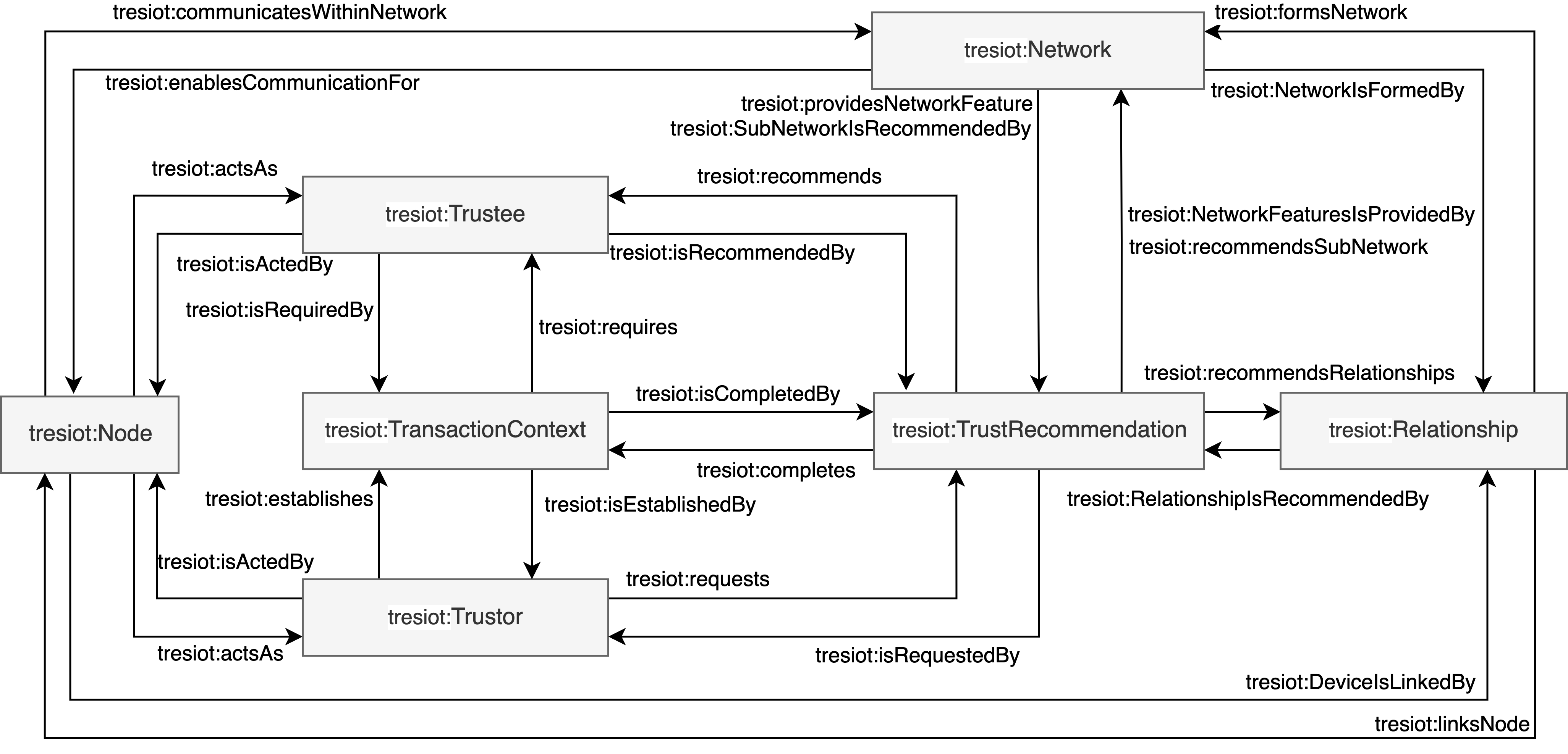
The node entity has relationships with the network and relationship entity to receive the required parameter to offer a holistic set of trust features. The node entity possesses trust features that might be relevant for trust recommendations of trustors towards trustees. The trustor entity initiates a request and establishes the transaction context. The trustor requires node features to obtain a trust recommendation to fulfill its trust-related objective and complete the transaction context. The transaction context entity refers to the specific circumstances of a transaction. The transaction context is established by the trustor and requires a trustee. After establishing the transaction context, the trust recommendation entity completes the transaction context with the provided result. The trust recommendation entity is used to recommend relationships between devices, the delegation of trustee, and communities. The trust recommendation is invoked by the trustor to evaluate the trustworthiness of the service provider. The service provider entity provides a service to a service requestor. In the context of trust recommendation, a service provider is required by the transaction context and is evaluated by the trust recommendation. The network entity relates devices and relationships to the network. The relationship entity is the result of a trust recommendation of a service requestor towards a service provider. Consequently, the relationship is established between devices and serves as a part of the network.
Trust Recommendation
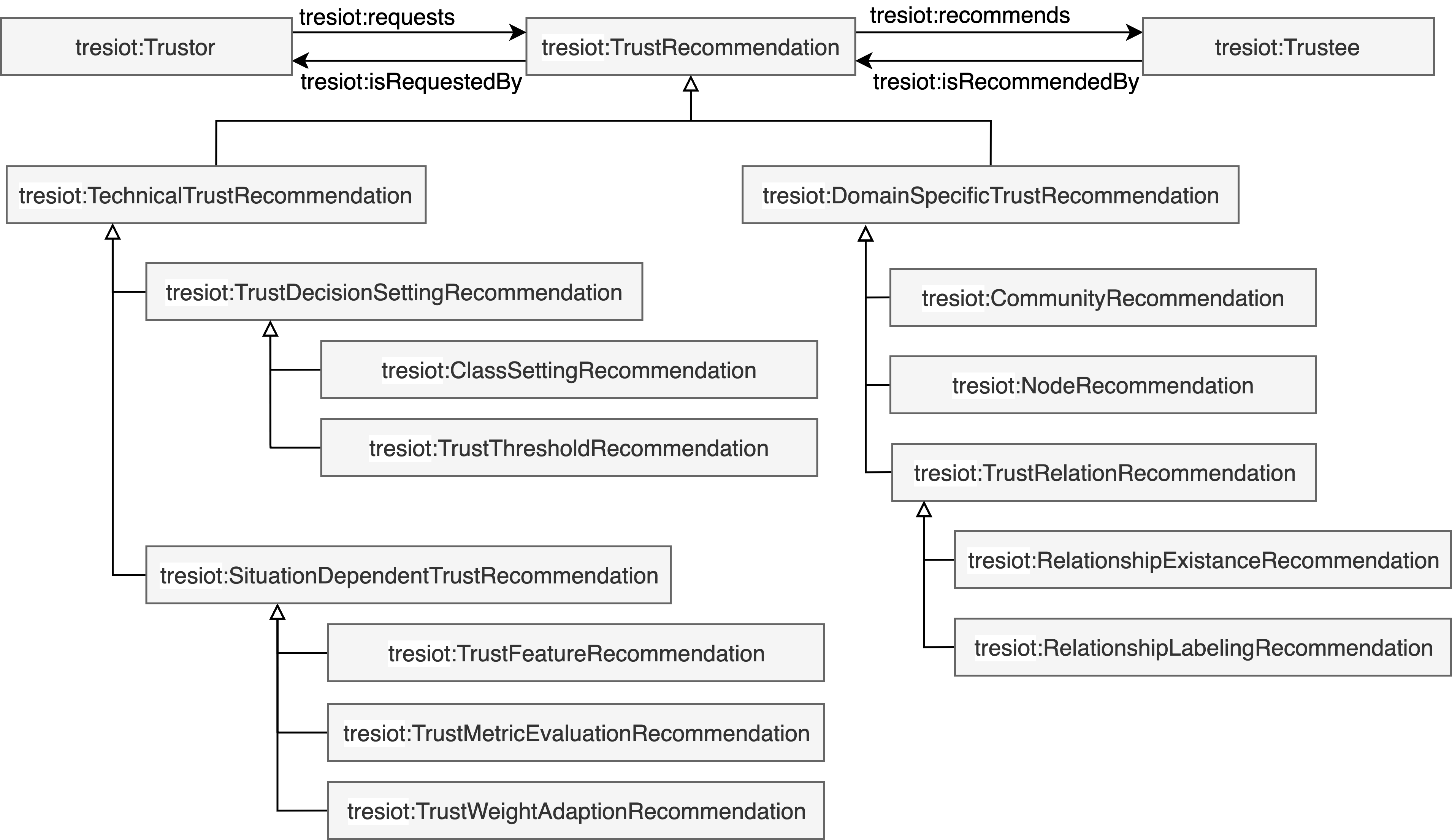
The trust recommendation ontology consists of the trust computation, the trust decision, and the trust review components as presented in Figure 8. Trust computation refers to the process of calculating a numerical value or score that represents the level of trust in a specific node. The trust computation summarises the concepts of trust evaluation and trust inference. We define the ability to employ observation and subjective experiences from the local transaction context between the trustor and trustee as trust evaluation models. In contrast, trust inference models utilize observation and experiences from the local and global transaction contexts to recommend trust values. This ontology further uses the categorization of trust computation methods from the literature (Becherer, 2024). In detail, trust evaluation has subcategories such as knowledge-based and context-aware methods. Knowledge-based methods are subdivided into network-based methods and perception-based methods. While network-based methods consider quality-of-service metrics to evaluate trust, perception-based trust evaluation models use social network metrics to establish trustworthy links without applying performance metrics. Context-sensitive trust models utilize additional contextual information from the environment to compute trust values more accurately. Therefore, domain-constraint and generic-based trust evaluation models are defined to distinguish contextual trust models based on their applicability. Beyond the social features of trust inference models in the SIoT, activity-based trust inference models utilize information on its operating environment to identify similar recommendations and trustors. The computation of activity-based inference methods uses distance-based and key-based similarity measurements. The SIoT is a network-oriented topology based on social attributes. Therefore, trust inference methods take advantage of social attributes to establish new relationships between nodes according to their similarity. Network-based trust inference methods are subdivided into feature-based trust inference methods concerning certain features to infer trust values and model-based trust inference methods that use attributes and relationships to establish new relationships and infer trust values. Several studies infer trust features from a social network or contextual feature perspective and employ both perspectives to form the mixed method category. While the trust computation entity computes trust value, the trust decision uses those computed trust values and conducts a trust decision. Therefore, certain trust decisions utilize a threshold-based approach to filter the service providers according to a particular set of criteria. Furthermore, a trust decision requires a ranking strategy to determine the service provider. The trust review assesses if the recommendation has been correct. Depending on the application of the trust recommendation, trust indicators can measure the success and suitability of the trust recommendation. The trust indicator usually has a name, a description, and a value.
Transaction Context
The transaction context captures all entities which are relevant to create a transaction and enable trust recommendations for various applications and describes the sequence to commit a trust transaction towards the trust system as presented in the figure below. The service requestor establishes the transaction context, which requires a service provider. The trust recommendation completes the transaction context through the computation of various service provider candidates and finally conducts a trust decision based on the task objective. Consequently, the transaction context creates the trusted device network
The transaction context itself has the attributes of the timestamp after the transaction context is completed, the trust value, the service providers, the service requestors, as well as the requested function of the service provider. Besides, the transaction context is related to the tresiot:representationOfTrustValue entity to enable various representations of the trust value. More specifically, the trust value has a numerical or descriptive representation, whereas the numerical representation can be interval-based or in an undefined range.
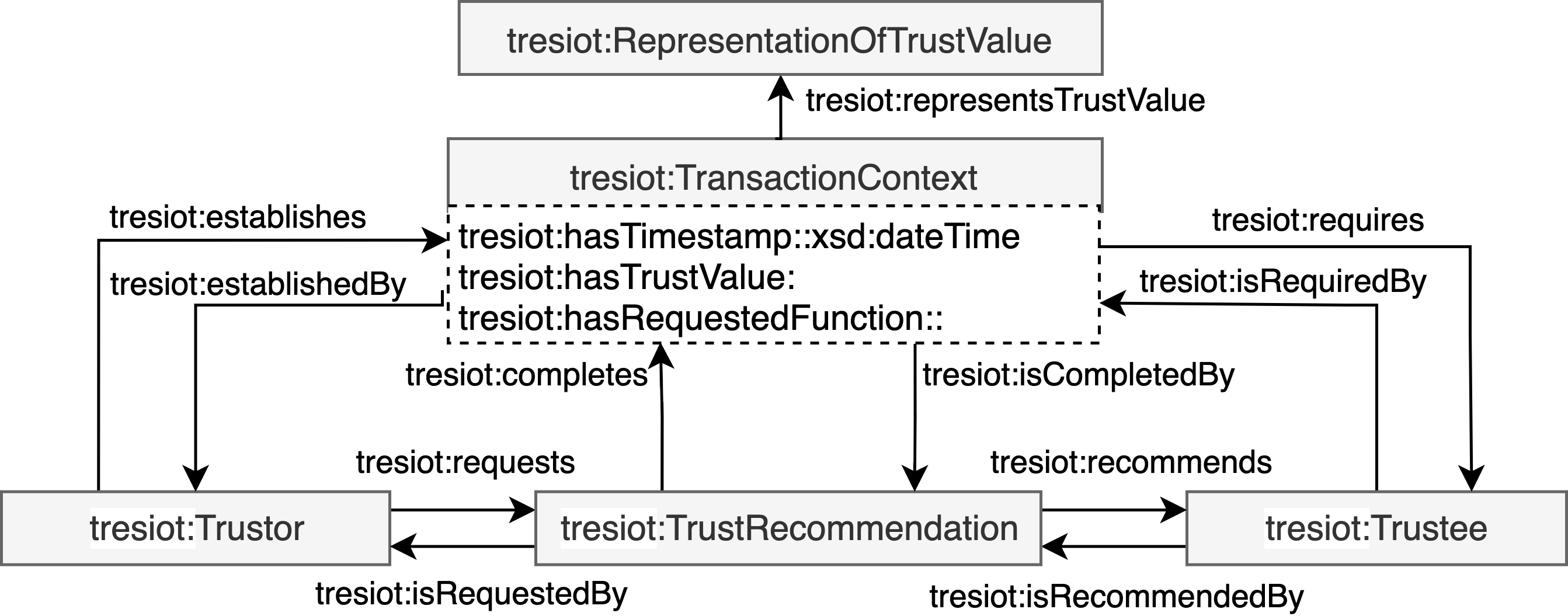
Relationship
The relationship concept consists of attributed-based relationships and experience-based relationships as presented in Figure 10. Attribute-based relationships between devices can bootstrap a trusted device network without experience from previous interactions. Therefore, node features enable attribute-based relationships between two nodes. The literature identifies attribute-based relationships, such as co-location relationship, social object relationship, co-work relationship, parental object relationship, and owner-object relationship. This ontology also proposes certificate-based relationships to enable relationships between devices within organisations. The combination of multiple node features enables the identification of further attribute-based relationships.
In contrast to attribute-based relationships, experience-based relationships emerge from the transaction context between the service provider and the service requestor. The experience-based relationships consist of the subjective-based experiences and objective-based experiences. The subjective-based experiences category includes only the local transaction context of one node that acts as trustor and interacts with different trustees. Hereby, the node can experience direct trust if the node has been involved within the transaction context and |edge_distance| = 1. Within the local transaction context, a node also can receive recommendations from related nodes within its network. Those nodes can provide direct recommendations where the recommending nodes have been involved in a direct trust transaction, whereas the |edge_distance| = 2. The indirect recommendation is a recommendation from a related node to the recommending node to the local transaction context of the node, whereas the |edge_distance| = 3. Longer distances than |edge_distance| = 3 can be created by concatenating direct trust, direct recommendation, and indirect recommendation.
The objective-based experience collects all experiences about one node from the overall network and includes various levels of granularity on a device, service and function level. The trustworthiness of all functionalities of a service makes the service itself trustworthy. Consequently, the trustworthiness of all services on a device causes the trustworthiness of the device.
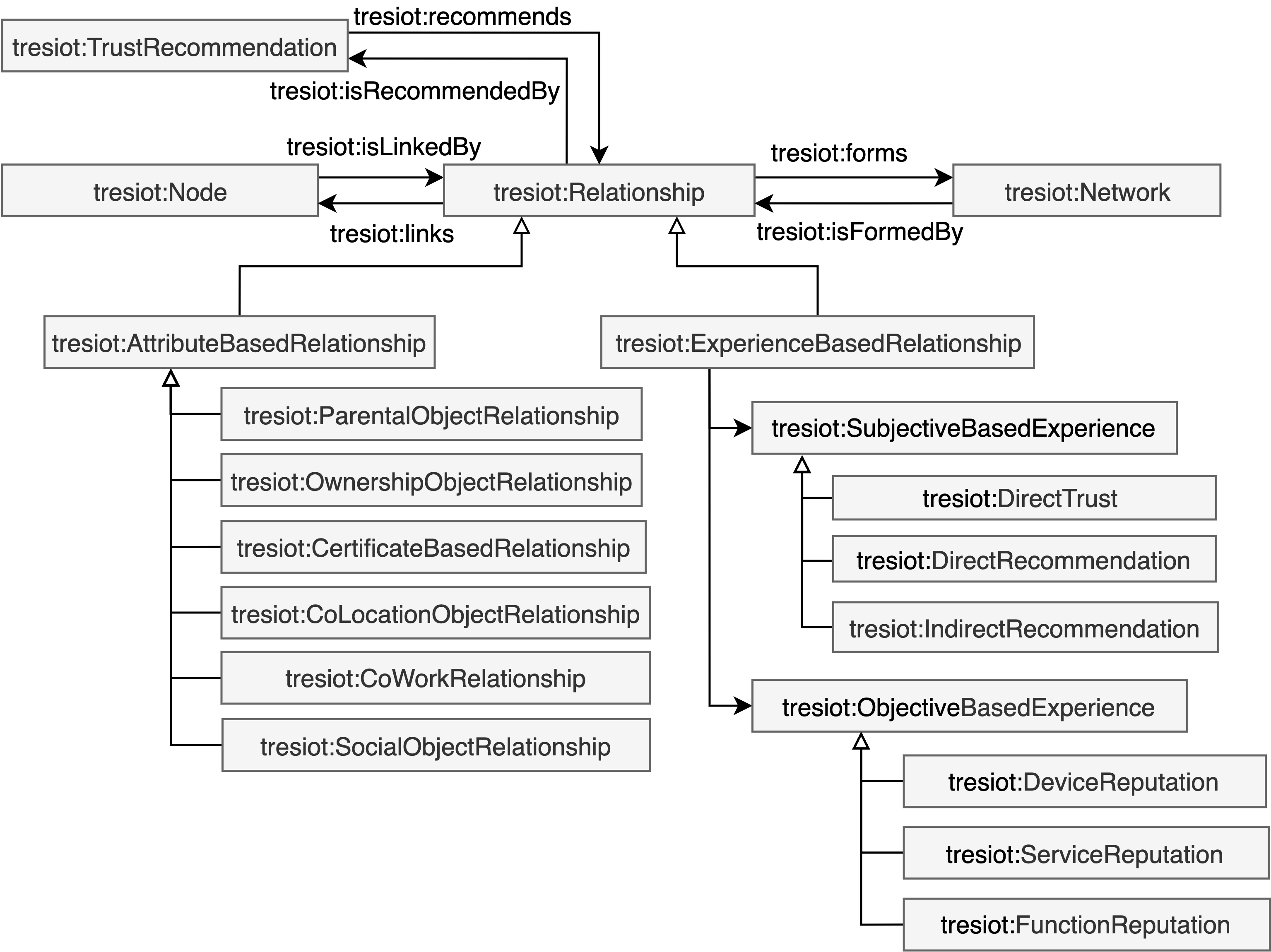
Network
The edge feature entity contains physical network parameters and social network parameters. The network packet property enables the physical network parameters. The physical network parameters contain time-related parameters, network traffic parameters, and delivery parameters. Time-related parameters include response time and latency. Network traffic parameters consider throughput, cumulative bandwidth average, retransmission rate, and package overhead ratio. The delivery parameters consider delivery ratios, such as the ratio of successful transactions and the ratio of failed transactions, the package transmission rate and the dropped package ratio. The Social network parameter of the edge entity considers the social trust parameter and tie strength formed by experiences from previous transactions, as well as network similarity that utilizes the whole trusted device network. In detail, the social trust parameters contain credibility and honesty. Honesty refers to the degree to which a device, service requestor, or service provider is the accuracy of the delivered information. Honesty is determined through direct experiences from previous transactions. While honesty represents a general concept in trust computing, the quantification depends on the individual settings of the trust model. Credibility refers to the degree to which a device, service requestor, or service provider is reliable and trustworthy. While honesty represents the data accuracy shared by IoT devices, credibility refers to the trustworthiness and reliability of the devices that deliver those data. The tie strength is usually measured by the degree of interaction frequency or length. Experience-based relationships enable the quantification of the tie strength attribute. The network similarity measures local metrics that deviate from graph theory, such as cooperativeness and centrality. Cooperativeness refers to the willingness of devices or entities to work together towards a common goal. Therefore, cooperativeness can be determined by the degree of common friends between nodes (Bao, 2011). Centrality refers to the relative importance or influence of a device or entity within the network and is described in degree, closeness, and betweenness centrality. Degree centrality measures the number of relationships a node has within a network. Nodes with a high degree of centrality are well-connected within the network. Closeness centrality calculates how close a node is to all other nodes in the network. Nodes with a high closeness centrality are well-connected to other nodes in the network and can quickly access and share information with them. Betweenness centrality describes how often a node acts as an intermediate node between other nodes in the network. Nodes with a high betweenness centrality have a central role in the network to enable trust recommendation between other nodes.
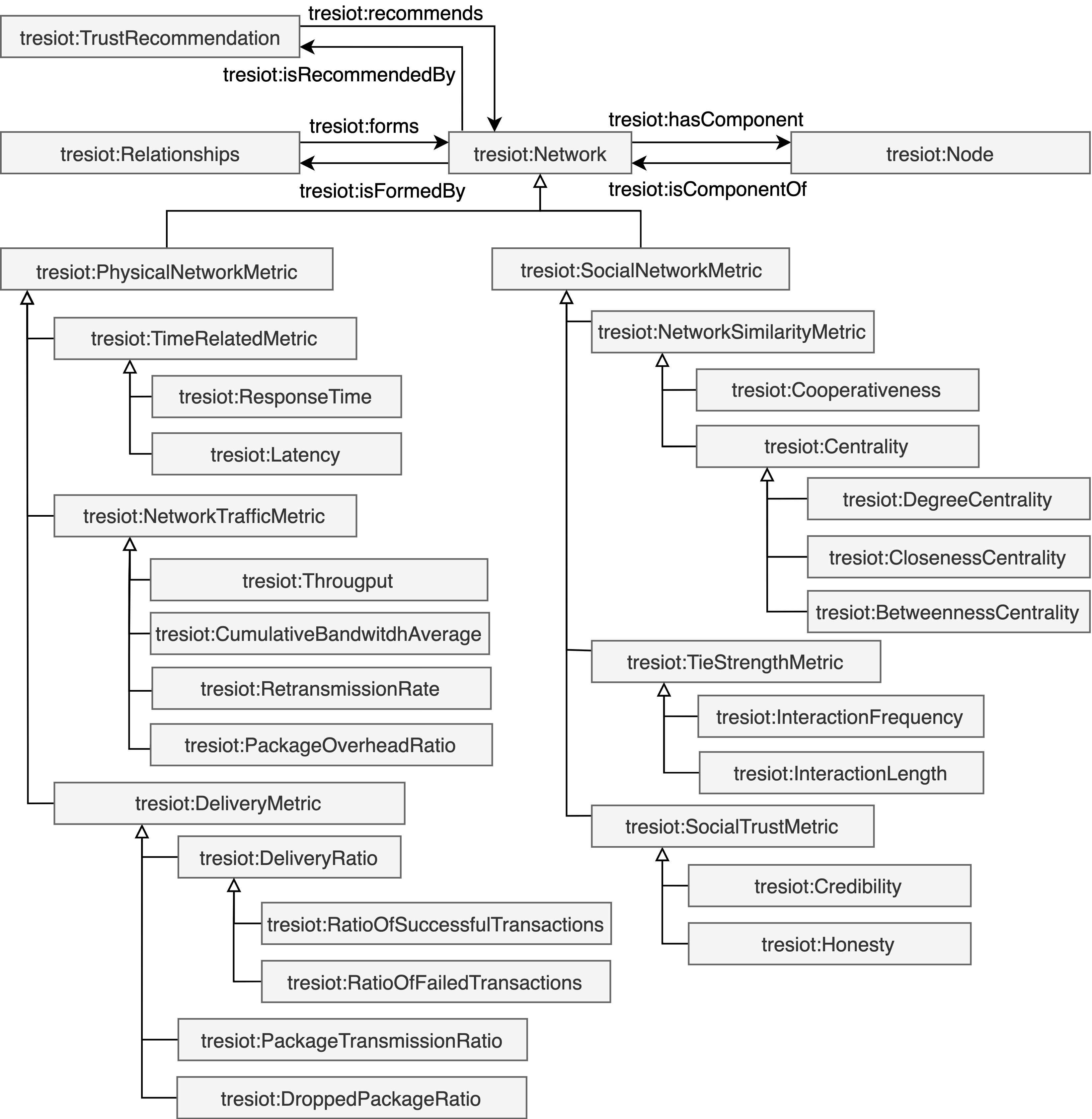
Node
The node concept can be instantiated as a device, service, or function to offer different granularity levels. The node concept is a network component and is linked with other nodes through relationships. Furthermore, a node has the capability to act as and trustor or trustee based on the role of the interaction.
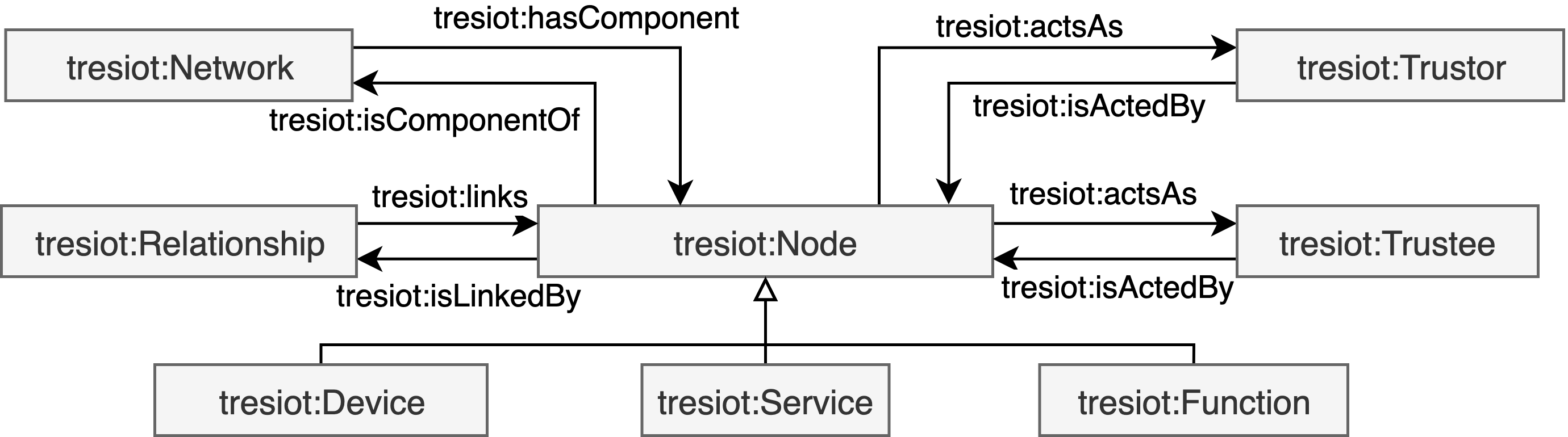
Trustor and Trustee
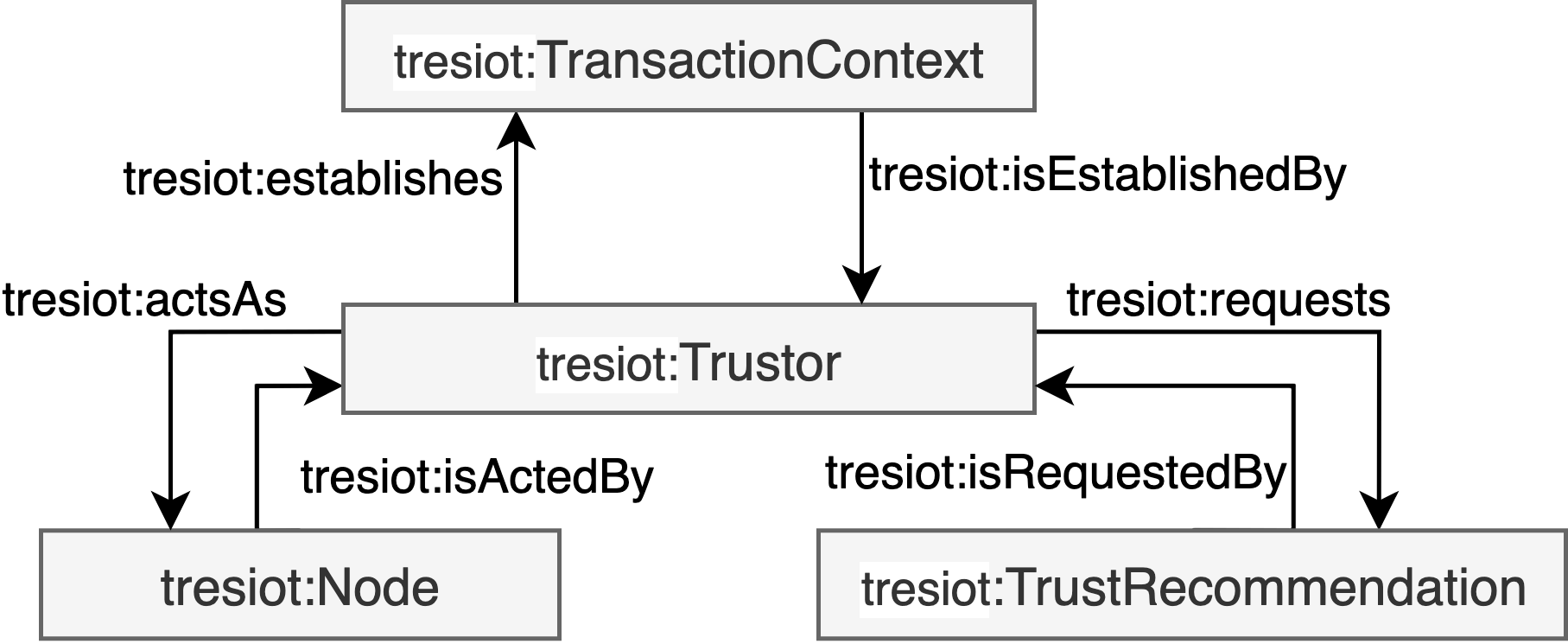
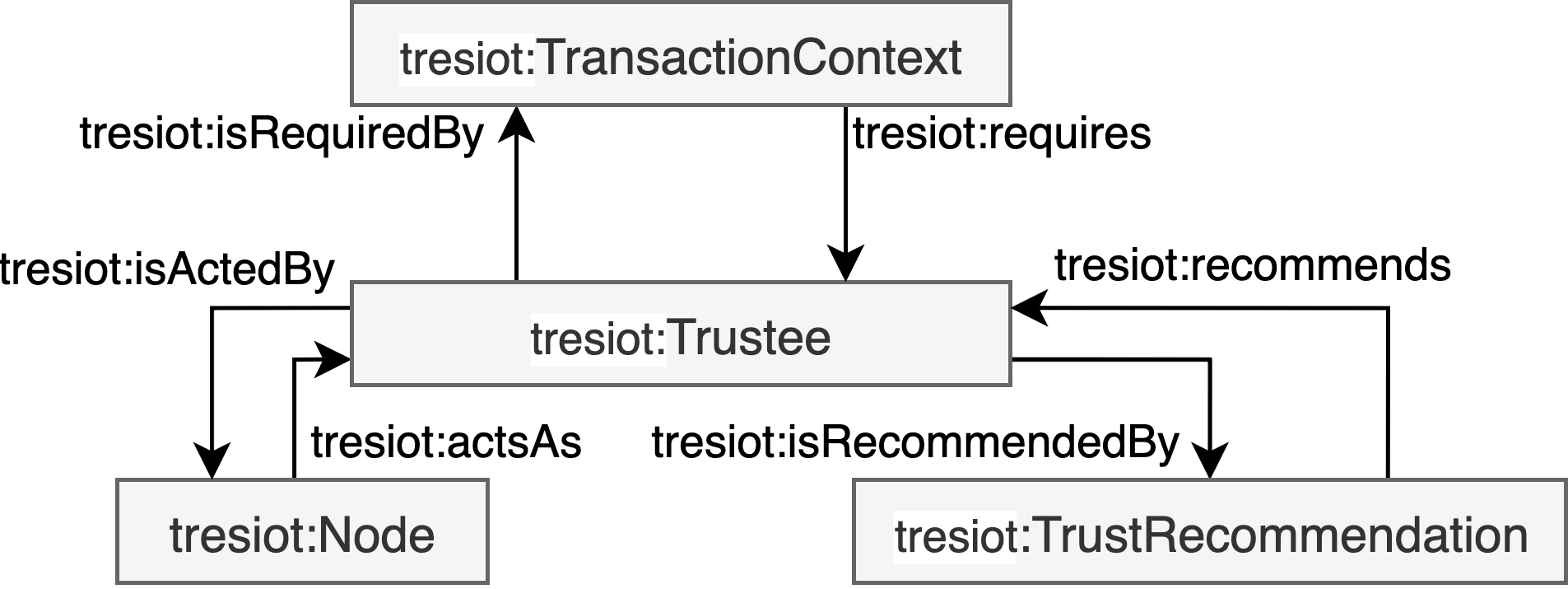
The trustor is a deliberate agent that aims to fulfill its objective by relying on the actions of another agent who appears to be willing and capable to support the trustor based on the agreed conditions in a given environment as illustreated in the figure below. The trustee is a capable and willing agent to produce outcomes based based on requested actions from trustors in a given environment as illustreated in the figure below.